As published on the Hunton Privacy and Information Security Law blog, on June 27, 2018, the Ministry of Public Security of the People’s Republic of China published the Draft Regulations on the Classified Protection of Cybersecurity (网络安全等级保护条例(征求意见稿)) (“Draft Regulation”) and is seeking comments from the public by July 27, 2018.
Pursuant to Article 21 of the Cybersecurity Law, the Draft Regulation establishes the classified protection of cybersecurity. The classified protection of information security scheme was previously implemented under the Administrative Measures for the Classified Protection of Information Security. The Draft Regulation extends targets of security protection from just computer systems to anything related to construction, operation, maintenance and use of networks, such as cloud computing, big data, artificial intelligence, Internet of Things, project control systems and mobile internet, except those set up by individuals and families for personal use.
The obligations of network operators include, but are not limited to (1) grade confirmation and filing; (2) security construction and ratification; (3) grade assessment; (4) self-inspection; (5) protection of network infrastructure, network operation, and data and information; (6) effective handling of network safety accidents; and (7) guarding against network crimes, all of which vary across the classified levels where the network operators are graded.
Network Operator Compliance
- Classified Levels. The network operator must ascertain its security level in the planning and design phase. The network is classified by five levels for the degree of security protection as shown below.
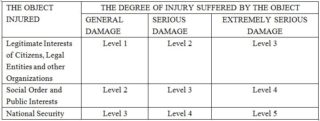
Explanation of terms such as “object” and “degree of injury” can be found in Draft Information Security Technology-Guidelines for Grading of Classified Cybersecurity Protection, which closed for public comment on March 5, 2018.
- Grading Review. The considerations for classified level grading include network functions, scope of services, types of service recipients and types of data being processed. For networks graded at Level 2 or above, the operator is required to conduct an expert review and then obtain approval from any relevant industry regulator. Cross provincial or national uniform connected networks must be graded and organized for review by the industry regulator.
- Grading Filing. After grading review, any networks graded at Level 2 or above must file with a public security authority at, or above, county level after confirmation of the classified level. The filing certificate should be issued after satisfactory review by the relevant public security authority. The timeline for the relevant public security authority to review such applications is not defined in the Draft Regulation, and is within the authority’s discretion.
- General Obligations of Cybersecurity Protection. Most of the general cybersecurity obligations are stated in the Cybersecurity Law, and the Draft Regulation stipulates additional obligations, such as:
- In the event of detection, blocking or elimination of illegal activity, network operators must prevent illegal activity from spreading and prevent the destruction or loss of evidence of crimes.
- File network records.
- Report online events to the local public security authority with jurisdiction within 24 hours. To prevent divulging state secrets, reports should be made to the local secrecy administration with jurisdiction at the same time.
- Special Obligations of Security Protection. The networks graded at Level 3 or above require a higher standard for their network operators, which will bear general liability and special liability, including:
- designating the department of cybersecurity and forming a level-by-level examination system for any change of network, access, operation and maintenance provider;
- reviewing the plan or strategy developed by professional technical personnel;
- conducting a background check on key cybersecurity personnel, and confirming those personnel have relevant professional certificates;
- managing the security of of service providers;
- dynamically monitoring the network and establishing a connection with the public security authority at the same level;
- implementing redundancy, back-up and recovery measures for important network equipment, communications links and systems; and
- establishing a classified assessment scheme, conducting such assessments, rectifying the results, and reporting the information to relevant authorities.
- Online Testing Before Operation. Network operators at Level 2 or above must test the security of new networks before operation. Assessments must be performed at least once a year. For new networks at Level 3 or above, the classified assessment must be conducted by a cybersecurity classified assessment entity before operation and annually thereafter. Based on the results, the network operators must rectify the risks and report to the public security authority with its filing records.
- Procurement. The network products used for the “important part” of the network must be evaluated by a professional assessment entity. If a product has an impact on national security, it must be checked by state cyberspace authorities and relevant departments of State Counsel. The Draft Regulation does not clearly define what the “important part” of a network means.
- Maintenance. Maintenance of networks graded at Level 3 or above must be conducted in China. If business needs require cross-border maintenance, cybersecurity evaluations and risk control measures must take place before performance of such cross-border maintenance. Maintenance records must be kept for public security’s inspection.
- Protection of Data and Information Security. Network operators must protect the security of their data and information in the process of collection, storage, transmission, use, supply and destruction, and keep recovery and backup files in a different place. Personal information protection requirements in the Draft Regulation are similar to those found under the Cybersecurity Law.
- Protection of Encrypted Networks. The networks relatng to state secrets are governed by encryption protection. Networks graded at Level 3 or above must be password protected and operators must entrust relevant entities to test the security of the password application. Upon passing evaluation, the networks can run online and must be evaluated once a year. The results of the evaluation must be filed with (1) the public security authority with its filing record and (2) the cryptography management authority where the operator is located.
Powers of the Competent Authorities
In addition to regular supervision and inspection, the Draft Regulation gives the competent authorities more powerful measures to handle investigations and emergencies. During an investigation, when necessary, the competent authorities may order the operator to block information transmission, shut down the network temporarily and backup relevant data. In case of an emergency, the competent authorities may order the operator to disconnect the network and shut down servers.
Penalties for Violations
The Cybersecurity Law includes liability provisions for violations of security protection, technical maintenance, and data security and personal information protection, as well as enforcement of the Draft Regulation. The Penalties include rectification orders, fines, relevant business suspension, business closing or website shut-down pending rectification, and revocation of relevant business permits and/or licenses.
The Hunton Blockchain Blog features opinions and legal analysis as we follow the development and use of distributed ledger technology known as the blockchain.
Search
Recent Posts
Categories
Tags
- 2019 Leaders’ Declaration
- 2020 National Strategy for Combating Terrorist and Other Illicit Financing (the 2020 Strategy)
- Advancing Innovation to Assist Law Enforcement Act
- Airdrops
- AML compliance program
- AML/CFT
- Anonymity-Enhanced Cryptocurrencies
- Anti-Money Laundering
- Anti-Money Laundering Act of 2020 (AMLA)
- Anti-Money Laundering Compliance
- Antifraud
- Aon and Marsh
- Arizona
- Arkansas
- Artificial Intelligence
- Artificial Intelligence (AI)
- Australia
- Australian Competition and Consumer Commission (ACCC)
- Australian Securities and Investments Commission (ASIC)
- Automated Clearing House (ACH)
- Bank of England
- Bank Secrecy Act
- Bank Secrecy Act (BSA)
- Bank Term Fund Program
- Bermuda
- Biden Administration
- BIS
- Bitcoin
- Bitcoin Cash
- Bitfinex
- BitLicense
- Blockchain
- Blockchain Incubators
- Blockchain Legislation
- Blockchain Regulatory Certainty Act
- Blockchain Technology Act
- Brazil
- Breach of Contract
- Broker-Dealer
- Broker-Dealers
- BSA
- BSA Enforcement
- BTFP
- Bureau of Economic Analysis
- Business Court
- California
- Canada
- Captive Insurance
- CCPA
- Celebrity Endorsers
- Central Bank
- Central Bank Digital Currency (CBDC)
- Centre for Information Policy Leadership (CIPL)
- CFTC
- Chapter 15
- China
- Christopher Giancarlo
- Civil Enforcement
- Class Actions
- Clearweb
- Colorado
- Commissioner
- Commodity Exchange Act
- Commodity Exchange Act (CEA)
- Commodity Futures Trading Commission
- Complaint Bulletin
- Compliance
- Compliance Note
- Congress
- Connecticut
- Consent
- Consumer Financial Protection Bureau (CFPB)
- Consumer Protection
- Convertible Virtual Currency
- Corporate Compliance
- Corporate Governance
- Corporate Transparency Act (CTA)
- Council of Institutional Investors
- Council of the European Union
- Countering the Financing of Terrorism (CFT)
- Covered Stablecoins
- Cross-Border Data Transfer
- Crypto
- Crypto Arbitrage Trading accounts
- Crypto Assets
- Crypto Bank
- Crypto Custody
- Crypto Hackers
- Crypto Mining
- Crypto Task Force
- Crypto-commodity
- Crypto-currency
- Cryptoassets
- Cryptocurrency
- Cryptopia Limited
- Cryptosweep
- Custodial Arrangements
- CVCs
- cybercrime
- Cybersecurity
- Dalia Blass
- DAO Report
- Darknet
- darknet marketplaces
- Data Privacy
- Data Protection Authority
- Davos
- Debanking
- Decentralized Finance (DeFi)
- DeFi
- Del. Michael San Nicolas
- Delaware
- Department of Business and Industry
- Department of Justice
- Department of Treasury
- DFS
- Digital Asset
- Digital Asset Securities
- Digital Assets
- Digital Commodities Consumer Protection Act of 2022
- digital currency
- digital currency ATM operators
- digital currency exchangers
- digital currency flows
- Digital Financial Assets Law (the Act)
- Digital Financial Technology
- Digital Token Act
- digital token sales
- Digital Tokens
- Distributed Ledger
- Division of Corporation Finance
- Documentary Stamp Tax (DST)
- Dodd-Frank
- DOJ
- Economic Sanctions
- EDPB
- Eleventh Circuit
- Endorsement Guides
- Enforcement Action
- ePrivacy
- Ether
- Ether Classic
- EU General Data Protection Regulation (GDPR)
- EU Regulation
- European Central Bank
- European Commission
- Exchange Act
- Exchange Traded Fund
- FDIC
- Federal Agencies
- Federal Election Commission
- Federal Reserve
- Federal Reserve Board
- Federal Trade Commission
- FedNow
- fiat currency MSBs
- Fiat-Backed
- Fight Illicit Networks and Detect Trafficking Act
- Figure Lending LLC
- Final Guidance
- Financial Action Task Force (FATF)
- Financial Crimes Enforcement Network (FinCEN)
- Financial Institutions
- Financial Privacy
- Financial Stability Board
- Financial Stability Oversight Council
- Financial Stability Report
- Financial Technology Protection Act
- FinCEN
- FINRA
- FinTech
- Florida
- Foreign Corrupt Practices Act (FCPA)
- Foreign Extortion Prevention Act (FEPA)
- Form 1099-DA
- Form BE-12
- fractional interests
- FTC
- Gemini Dollar
- Gemini Trust Company
- GENIUS Act
- Global Consortium for Digital Currency Governance
- Group of Seven
- Group of Twenty (G20) Finance Ministers
- H.R. 5635
- Hard Fork
- Heath Tarbert
- Her Majesty’s Revenue & Customs (HMRC)
- HM Revenue & Customs (HMRC)
- Home Equity Lines of Credit (HELOCs)
- Homeland Security Assessment of Terrorists’ Use of Virtual Currencies Act
- House of Representatives
- House of Representatives’ Financial Services Committee
- Howey
- Howey test
- IEO
- iFinex Inc.
- Illinois
- India
- Information Sheet 225
- Initial Chain Offering
- initial exchange offerings (IEOs)
- Insurance
- Intellectual Property
- International
- International Monetary Fund (IMF)
- Investor Protection
- IRS
- Jefferies Funding LLC
- Kenneth Blanco
- Kentucky
- KYC/AML requirements
- Lael Brainard
- Large Platform Utility
- Legislation
- Legislature
- Liechtenstein Parliament
- liquidity
- Litecoin
- Litigation
- Louisiana
- Ltd.
- Malicious Cyber Activity
- Malicious Cyber Actor
- managed stablecoin
- Martin Act
- Maryland
- Metaverse
- Mississippi
- Model Money Transmission Modernization Act
- model rule
- Monetary Policy
- Money Laundering
- Money Service Business
- money services businesses (MSBs)
- Montana
- Mortgages
- Multi-Level Marketing Program (MLM)
- Mutual Fund
- Nakamoto
- narcotics
- NASAA
- Nebraska
- network maturity
- Nevada
- New Jersey
- New York
- New York Attorney General
- New York Department of Financial Services (DFS)
- New Zealand
- NFT (Non-Fungible Token)
- NFTs
- No-Action Letter
- Non-fungible tokens
- North Dakota
- North Korea
- NY Department of Financial Services
- OFAC
- Office of Investor Education and Advocacy
- Office of the Comptroller of the Currency (OCC)
- Ohio
- Oklahoma
- Patent
- Paul Atkins
- Paxos Standard
- Paxos Trust Company
- Peer-To-Peer Exchangers
- Penalty
- Pennsylvania
- Personal Data
- Personal Information
- President Trump
- President’s Working Group (PWG)
- Privacy
- privacy coins
- Proof-of-Stake
- Provenance.io
- Proxy Voting
- Public Blockchain
- Rapid Settlement
- Real Estate
- Regulation and Enforcement
- Rep. Sylvia Garcia
- Rescission
- Retail
- Ripple
- Ripple Labs
- Rule 233-1
- Russia
- Sanctions
- Sanctions Compliance Program (SHP)
- SAR lookback review
- SD8 coins
- SDN List
- SEC
- SEC Crypto-Securities
- SEC registration
- Securities
- Securities Act
- Securities Act of 1933
- Securities and Exchange Commission
- Securities and Exchange Commission (SEC)
- Securities Exchange Commission
- Security Tokens
- Security-Based Swap
- Self-disclosure
- Senate Banking Committee
- Senate Committee on Banking Housing and Urban Affairs
- Shareholder
- Shareholders
- SIFI
- Signature Bank
- Silicon Valley Bank
- South Carolina
- South Dakota
- Spencer Dinwiddie
- Stablecoins
- Stablecoins are Securities Act of 2019
- Staking Activities
- State-Sponsored Malicious Cyber Groups
- Suspicious Activity Report
- Suspicious Activity Reporting (SARs)
- SVB
- SWIFT messaging system
- Swiss Financial Market Supervisory Authority (FINMA)
- Switzerland
- Synthetic Hegemonic Currency
- Taxation
- Templum
- Tennessee
- Terrorist Financing
- Tether Limited
- Texas
- Texas Business Organizations Code (TBOC)
- Texas Senate Bill 1859
- Texas Senate Bill 1971
- The World Bank
- Three-Year Safe Harbor
- Token and TT Service Provider Act
- Token Developers
- Token Transfer Limits
- Tokenization
- Tokenized Assets
- Trademark
- Travel Rule
- Trump Administration
- TT Identifier
- TT System
- TVTG
- U.S. Virtual Currency Market and Regulatory Competitiveness Act of 2019
- UCC Article 12
- UK Tax Rules
- Unhosted Wallets
- Uniform Commercial Code
- United Kingdom (UK)
- United Specialty Insurance Company
- United States Bankruptcy Code
- United States Patent and Trademark Office
- US central bank digital currency (US CBDC)
- US Department of the Treasury
- US Department of the Treasury’s Office of Foreign Assets Control (OFAC)
- US dollar
- US Securities and Exchange Commission (SEC)
- US Treasury
- USTR
- Utah
- Vermont
- Virginia
- Virtual Asset Service Providers
- Virtual currencies
- Virtual Currency
- Virtual Currency Consumer Protection Act of 2019
- Virtual Currency Exchange
- Virtual Currency License
- Virtual Currency Tax Fairness Act of 2020
- Virtual Markets Integrity Initiative
- Washington
- Weapons of Mass Destruction Proliferators Sanctions Regulations
- World Economic Forum
- Wyoming
- XRP
Authors
- Jimmy Bui
- Mayme Donohue
- Andrew Feiner
- Jason Feingertz
- Hannah Flint
- Kevin E. Gaunt
- Armin Ghiam
- Carleton Goss
- Gregory G. Hesse
- Scott H. Kimpel
- Marysia Laskowski
- Michael S. Levine
- Lorelie S. Masters
- Patrick M. McDermott
- Uriel A. Mendieta
- Alex D. Pappas
- Daryl B. Robertson
- Natalia San Juan
- Caitlin A. Scipioni
